
 |
| |||||||
| Register | FAQ | The Twelve Commandments | Members List | Calendar | Arcade | Find the Best VPN | Today's Posts | Search |
| LimeWire+WireShare Tips and Tricks Advanced users meet here to share secrets about pushing LimeWire to the limit. |
 |
| | LinkBack | Thread Tools | Display Modes |
| ||||
| If you are looking for the Security Updaters, see post #38 (can click link) further below. Or use these links: LimeWire Security Updater installers via MediaFire, OR via Sabercat Not all the Japanese peers are good peers, but that's true for a number of countries I guess. In my connection lists I've posted for people having connection problems, I removed most Japanese hosts, only a few 'if any' left on the list from memory. I've done the same thing as you at times, continually removed such hosts. If you desperately wanted to get rid of Japanese hosts full stop, you could ban all their ranges. lol  I've tried that too. I've tried that too.Just as a note, I find Phex tends to get a nice mix of European and USA hosts. Not sure why LW attracts them, both LW 4 & 5, perhaps because it IS LW.  But LW was designed to give some preference to connecting to LW and LW clones (such as Cabos), also for search results. This is a common trait for most gnutella clients to be set to favor their own kind when they can. My Phex just connected to 3 French, 1 UK and 1 USA, then later a 6th ultrapeer. But LW was designed to give some preference to connecting to LW and LW clones (such as Cabos), also for search results. This is a common trait for most gnutella clients to be set to favor their own kind when they can. My Phex just connected to 3 French, 1 UK and 1 USA, then later a 6th ultrapeer.Here's a funny episode. Whilst using BearShare, I accidentally replaced my hostiles with the original and ... these hosts, each time I removed them they were replaced with more of same ip address or similar, example 3 snaps joined here (all same port, all same shares): snapshots joined. These are in fact what I refer to as Download-BOTs; they attempt to fill all your upload slots. Their program ID's are fake & not what they advertise themselves to be. The security Hostiles file(s) blocks these BOTs (edit: WireShare blocks them by default internally.) If you have a firewall that can ban ports such as Windows 7 firewall, I guess you could set up a disallow rule for port 6346 but this might also mean the possibility of missing out on some good hosts who are using port 6346 as a static port and not necessarily using Cabos or similar. But I would recommend banning ports 27016 and 7001 for both tcp and udp if you can, only LW spammers use that port. More on spam or bad addresses here http://www.gnutellaforums.com/open-d...tml#post368141. Note: the technutopia hostiles document itself is not read by any version of LW 5 due to its older address format layout. If you want a full list of Japanese ip's I can send you one privately. Or else send you the list I use for blocking many of them. The majority of Japanese ip addresses below the 200.x.x.x range are static and do not change. Edit: Port Block instructions I have included some instructions on how to block port 27016 in your firewall (you should also block port 7001.) This example applies to Windows 7 firewall but most 3rd party firewalls will probably have a similar option. (Note: whilst LW 5 might connect to many spammers using port 27016, both LW 4 and FrostWire are total magnets for them.) For Windows 7 and 8, go to Control Panel, open up Windows Firewall. Click on the Advanced Settings option. Once the Advanced Settings is open, look to the left-side and click on Inbound Rules. Now, shift your eyes to the right-side of the firewall window and look for the Actions section for Inbound Rules and click on New Rule underneath it. In the window that appears you will have 4 options for type of rule to add, choose Custom. Then click Next button. You can either specify All Programs or simply one here. Then click Next button. Protocol Type drop down menu: select TCP first (later do another identical rule for UDP.) Leave Local port set to All Ports. Then select Specific Ports option for Remote port and type in port 27016 into the port number box. Then click Next. Set Scope to Any ip address (leave it as it is.) Then click Next. The next window gives action choice. Check the option to Block the connection. Then cilck Next button. Check all the options for Domain, Private and Public, then click Next button. This is the final window giving you the choice to name and describe the new rule. Description is optional. Name it something that represents the new rule. I named mine Port Block 27016 TCP then click Finish. I would recommend you do a new equivalent rule also for UDP. It is possible to duplicate a rule, double-click it and then simply change the protocol from TCP to UDP and rename it appropriately. Port 27016 is not officially used for anything you would ever use it for. Port 27016 spammer hosts tend to use proxy switchers so there is little point in banning their ip's for longer than a week. Port 7001 is used by upload-slot container hostile hosts which not too many people know about, example image snapshots of upload attacks here and here.  (Click sample image to see larger view, click again to see in its own window unless you have pop-up blocker.) (Click sample image to see larger view, click again to see in its own window unless you have pop-up blocker.)* Sorry, last year I accidentally gave incorrect instructions for this. This is the correct way to block ports for Windows 7+8.  * This similar example might even be slightly better. * This similar example might even be slightly better.A Gnutella ip Group Block in Windows 7 or 8 Firewall Windows 7's firewall has the option for doing a group block. I created one for TCP and UDP. In fact, you only need to do one then duplicate it and change the rule's protocol from TCP to UDP then rename it or alternatively a single rule and set the protocol to All. Sounds easy?  Set up a new inbound rule, and set it to Custom in the window that appears. Choose either all programs or LimeWire/FrostWire, etc. path (my sample shows all programs but you can choose a specific program), then all ports. Then start adding the host addresses you wish to add. Then when finished, name the rule. I have created a sample image but note, the sample GiF is a little large in size and has quite a few frames. The advantage of a group block is you could disable it if or when necessary, or simply set it to only apply for LimeWire/FrostWire, etc. in the program/path option. For a good reference for hosts to block in a firewall see http://www.gnutellaforums.com/open-d...tml#post368141. Set up a new inbound rule, and set it to Custom in the window that appears. Choose either all programs or LimeWire/FrostWire, etc. path (my sample shows all programs but you can choose a specific program), then all ports. Then start adding the host addresses you wish to add. Then when finished, name the rule. I have created a sample image but note, the sample GiF is a little large in size and has quite a few frames. The advantage of a group block is you could disable it if or when necessary, or simply set it to only apply for LimeWire/FrostWire, etc. in the program/path option. For a good reference for hosts to block in a firewall see http://www.gnutellaforums.com/open-d...tml#post368141.Why would you block these ip's in your firewall? To reduce very high pings directly aimed at your program (such as LW), so the firewall handles it instead. This will mean less lag building up in LW over a period of time. It will also mean less chance of LW being affected by the pinging and drop its performance as a result. 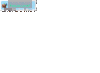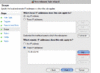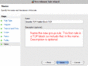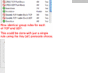 (sample GiF image 250 KB, click to see in large view) (sample GiF image 250 KB, click to see in large view) 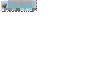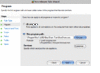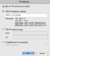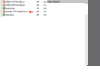 * (this sample only needs a single rule by using the 'Any' protocol and applied specifically to the program to be used for.) * (this sample only needs a single rule by using the 'Any' protocol and applied specifically to the program to be used for.)How to add an ip group block list to Kaspersky Firewall: Firewall -> Settings -> Network Packets -> select 'Addresses from Group' and click Add -> click Add to add an ip address and continue doing this. After adding all the addresses, name the rule something like 'ip address block list' & click OK. Make sure that rule is still selected in the Network Packets section and select 'Block' at top and 'Any Network Activity' in the middle section. Though you can select the Block option after selecting addresses from group option near beginning of the process. Later versions of Kaspersky Firewall might look a little different but the process will most likely be the same or similar. Kaspersky Firewall sample image (click to see sample image) Outgoing rules? Why set up outgoing rules to block certain ip ranges instead of only incoming rule blocks? Because if you are sharing files, your program sends your shared files details that correspond to a particular search. Do hostile clients search? Since some hostile clients are known to browse hosts, then chances are they also do searches. Hosts with port - 7001 are known as upload-slot containers, they will download everything you have, they get paid to do this to prevent you sharing to anybody else. Having equivalent outgoing rules may help to slightly reduce some incoming traffic from bad hosts. (I also strongly suspect 'they' have BOTs that search the network and every client they can find.) Replicating incoming block rules for outgoing rules has an effect of keeping you partially invisible to hostile hosts. This also applies to the ports 27016 and 7001 block rules. I have found the outgoing rule for port 27016 UDP ping count now out-numbers the incoming. And some other blocks now count as zero incoming but high numbers outgoing. This suggests your shares details have been blocked from being sent to 'them' if you also choose to use firewall outgoing block rules. This also helps with reduced spam results, overall better performance without receiving as many pings from the hostile hosts. There was a very noticeable increase in search results (two to three times more than average in initial testing.) If running as an ultrapeer, then leafs in search mode.should arguably be receiving less results from bad hosts via searches that touch your client in any way. Last edited by Lord of the Rings; February 15th, 2013 at 06:08 AM. Reason: Re-did my Windows 7 port block sample, since my original was incorrect. Added: Outgoing firewall rules a major plus !!! |
| ||||
| Quote:
There was a LimeWire Beta version, one of the 5.5/5.6 prototypes called Geo-Restrict which I believe was supposed to have the purpose you are asking. http://www.gnutellaforums.com/gettin...-5-5-16-a.html, ie: released on May 4, 2010. The only prototypes version I've tried in recent times was the Light version which was designed to use less computer resources than standard LW. |
| ||||
| Quote:
|
| ||||
| Oops I accidentally left 3 large ranges off the list yesterday, I've replaced the list. Sorry about that, because I know a few people downloaded it.  In my experience, LW 5 does not appear to be able to read a range x.x.x.x/11 or larger to /1. Thus I needed to split those ranges up into /12 blocks which represents x.0.0.0.0 . to . x.15.255.255 for example. I accidentally left 3 of those out of the shortened list since the longer list had /8 and I removed those when I reduced the list. Anyway, it's fixed. Edit again, I fixed up a few other small errors. duh, sloppy work. I redid the list instead of using the one I had which is where errors crept in. I've amended it about 3-4 times now. I should have simply grabbed the ones from my firewall since they were all correctly done. And sorry again, I've been cursing myself for my errors. We all make mistakes.  Remember if you are copying this list to the end of any existing ban list, the last address of your existing list will need a semi-colon ; before you copy these to the end of that list. All addresses should be separated by a semi-colon with exception of the very last one on the list. If you wanted to extend the filter further if too many hosts are getting through, then add the addresses with /19 at the end. That would take the total of listings up to 1,095. Or even also the /20. This is one reason I supplied the full list to refer to just in case. For anybody who is wondering: /32 = 1 single ip address. /31 = 2 sequential addresses. /30 = 4 sequential addresses. etc. As you notice the range keeps doubling. Continuing to /24 =256 addresses, /23 = 512 addresses, etc. I've confirmed BearShare 5 cannot read this ip addressing format. BS instead uses an older sub-net masking format. Edit: BTW if you installed/pasted my earlier postings of the blocklist, then you can remove them. Open the Japan & Taiwan block list file and choose the first host address listed near top of page, select and copy it. Then open the Limewire.props file, open the search function and paste the host address you copied into the search box. Then search. Then select that found first address and whilst holding the SHIFT key select to the last of them and delete/cut/remove. The first address will be 1.0.64.0/18 and the last address will be 223.223.0.0/17. The numbers are all in numerical order so should be easy to find the last one. You can then replace that with the newer list. I have an upcoming Shortened 'Hostiles' list from the BearShare Full-size Hostiles blocklist I will post soon. I am trying to make sure there is no needing to repost with this next block list, unless it is an updated version. As you might expect though, the Hostiles list is quite large. Even though it's a fraction of the half-million listings of the original.  But I have tested the hostiles list with the additional Japan+Taiwan list also added and so far no memory issues, surprisingly. I will leave it running to see how it goes over an extended period. But I have tested the hostiles list with the additional Japan+Taiwan list also added and so far no memory issues, surprisingly. I will leave it running to see how it goes over an extended period.My newer note for the Hostiles list will explain the two main areas that cause memory problems with LW 5 / LPE. And what to reduce if you do have LW memory problems. Reducing your hair, a haircut is always good even if it does not help LW.  Last edited by Lord of the Rings; August 10th, 2012 at 03:27 PM. Reason: Edited to give up to date details |
| ||||
| I quite easily connect as an ultrapeer. If I don't, I find that if I close LW and restart this can often help invigorate LW into becoming an ultrapeer. That's for LPE at least. Not sure this approach is so great though since UP's are supposed to be users whom are in a way rewarded for their long times online. Sure I spend 1-4 sequential days online. But, LPE seems to be able to be kicked into UP sometimes. If I restarted LW after a long session and it starts to connect as a leaf, if I remove the UP's as it's connecting it can also kick LW into UP mode. But I will confirm Sleepless's advice on page 1 of this thread still works for LimeWire 5. After an hour as a Leaf drop the first or second connections. Sometimes I may need to drop them all and this then pushes me into Ultrapeer mode (U.P.) And in my own experience, I seem to get much better search results and less spam when running as an ultrapeer. For example, when as a U.P. over the past two years I tend to get 50-60 results (and if it's 90-110 then I know I'm with good connections) for a particular search term I often use. When as a Leaf I might only get 20-30 results for same search. The way LW is designed, normally connecting as an ultrapeer can depend on average time online (and not being firewalled of course.) I noticed this in the LW mediawiki. |
| ||||
| Edit: Since September 2015, there has been considerable removals of blocked ranges from the list. These listings appear to be redundant. Probably over 90% of the original listings were put in place prior to 2011 (or prior to 2010.) Obviously this needed to be reviewed. Since then, many internet service providers have changed owners; purposes for some ranges has changed; whilst last decade most ip addressing was static, nowadays the opposite is true, mostly dynamic; some companies set up for attacking the network no longer exist. But at the same time, some new companies have been found in recent years. There is now a combo WireShare-LimeWire Hostiles-Updater. The WireShare hostiles included within the program installer is from July 2015. The older WireShare versions' hostiles even older. (Original text from 2012): It has been a few months since I suggested I would do it. But I have finally created a blocklist (security list) based off the original BearShare Full Hostiles but continually updated over past few months. I realised the props file is a terrible place for a large amount of data to be stored because LW copies that information into memory and totally rewrites the data back to the props file every 5-10 minutes. (obsolete): Based on my work on the MacOSX Portable Mac, I had an inkling of an idea I might be able to force LW to read a settings option from a separate file. And it works! I recently packaged all the LW 4 and 5 installers with the security installers. These installers included with the LW installers include a base LW.props (settings) file which includes the directive path for LW to find and use the security file. (/obsolete) Nobody is pretending these files will block out all spam but definitely reduce it very significantly. I use the CIDR host format which is more memory friendly than the older netmask format BearShare uses (50-55% less memory.) Also my large (Strong) lists are notably smaller than the BearShare list but does not take any strength away. (My list is also smaller than the FW list which uses the old BS netmask format.) A comparison of characters needed in memory between the LW CIDR blocklist and the BearShare Full Hostiles: LW-NJ (441,000 hosts) = 6,609,430 BearShare Hostiles-NJ (477,000 hosts) = 14,042,472 LW full (418,000 hosts) = 6,259,398 BearShare Hostiles Full (453,000 hosts) = 13,320,053 LW-Light NJ (31,000 hosts) = 473,592 LW-Light (30,000 hosts) = 458,626 The security lists have been tested with LW 4.14 to 4.18 and LW 5 (Pirate Edition.) I presume the security lists will also work with earlier versions of LW 4. LW 4 and 5 seem to be able to handle the large security list fine, though for those with very large shares and whom have long sessions (several days) may find LW 5 becomes a little laggy after 2-3 days. There should be no problems using the large list in general. But if you do, swap to one of the light lists. The large list is about 14 times larger (I refer to the large list as Strong Security.) I will be updating the Security files every 4 to 6 months. (- edit). I will date them so you know. With 6 lists to update (two for BearShare), it's a lot of work. Incredibly slow, tedious and boring.  I will not be adding spam hosts to the list unless they are sighted again after a month (but will keep a permanent record of them.) Some spammers use proxy switchers, and some other spammers use dynamic addresses. This bothers me about inheriting a previous list because I have no idea of the prior methodology used. Edit: If there had been enough interest shown I might have started from 'almost' scratch but seems not many persons have shown interest in this security concept. Not a bad idea to clear out any banned lists of spammers you have done after a week or month. Chances you will never see most of them again using the same host address after a day or a week. Clearing the list out will save on memory use. The 'Full' Japanese block versions are really 'full' blocks. There's only a very minor chance you might see any Japanese hosts. Yes you may see Cabos hosts but they will not be from Japan. Unlike my partial Japanese blocks I did a few months ago. If you used those previous Japanese block lists from 3 months ago you should remove them from your props file Banned list to save some memory. * I would recommend removing most if not all of your previously banned hosts to save memory. Using the Security list you will probably find any hosts you banned previously are no longer needed. You can still add fresh ones by the usual method of banning if any hosts are spammers or are problematic. (obsolete): Once your limewire.props file has the directive instructions for LW to find the location of the security file, after that in future all you need to do is install updates to the security file itself. Unless of course you delete your LW preferences folder for any reason or your LW props file becomes zeroed after a severe crash. (/obsolete) WireShare or LimeWire will not read or re-read a fresh hostiles file until after the program's next restart. So it's best to install the hostiles-update whilst the program is closed. The options: 1. 'Light' Security Choice for keeping things light. The main known static spam companies are blocked. Though you might still receive spam from dynamic/proxy spammers. Filename: LimeWire Light Security-NJ 2012 Windows Updater 2. 'Light' Security with 'Full' Japanese blocks for those whom only wish to connect to and search for similar cultural content. This will also remove any chance of spam from Japanese hosts. Filename: LimeWire Light Security 2012 Windows Updater 3. 'Strong' Security This will maximize blocks against spammers. Not to say you will not still get spam, but will greatly reduce it significantly. Filename: LimeWire Strong Security-NJ 2012 Windows Updater 4. 'Strong' Security with 'Full' Japanese blocks for those whom only wish to connect to and search for similar cultural content. This will also remove any chance of spam from Japanese hosts. This is the strongest of all the packages and is 6% smaller than the other Strong security package due to not needing to block individual or small ranges of known Japanese spam/hostile hosts. Filename: LimeWire Strong Security 2012 Windows Updater * In case you are wondering, the initials -NJ represent No Japanese blocks. Though really means just basic blocks against known static Japanese spammers and business ranges. But you will still be able to download and share with regular Japanese hosts. Windows users: (as of Feb 2013 only one installer): The installer gives the above 4 options. As of 31 April 2013, the updater will no longer replace your props file if first time installing. Instead the necessary instruction is inserted into the props file by the installer. (obsolete): If you would prefer to do it manually, then uncheck first option in the installer or download the separate zipped Linux security file of choice. Open your limewire.props file in your LW preferences folder and create a fresh line and type in the following: PATH_TO_BLACK_LISTED_IP_ADDRESSES=Home>AppData/LimeWire/Hostiles.txt Save the file as standard text, keeping the .props file extension. This line is necessary for LW to find the security file. If you simply install the security file and LW's props have no instructions on finding it then LW will not use the security file. (/obsolete) MacOSX users: all 4 packages are included within the one installer. Choose from the installer's menu options. The installer script will insert a line of text into your props file which will tell LW where to find the security file. This makes it very very easy for you. Filename: MacOSX LimeWire Security 2013 install-Updater Linux users: download the Linux security file of choice, unzip and place into your LW preferences folder found at: ~/.limewire Edit 8 June 2013, I have now included a .sh bash script for installing, all inclusive in one package. I used 7z format as it compresses to 1.3 MB compared to zip or tar.gz at 3.4 MB. Uncompress, open the folder and simply run the script via terminal and your choices will show. Line inserted into the props file for you. The manual method below is then not necessary. (I used bash v.4 syntax for suppressing i/o error messages, let me know if this causes problems for anyone using an earlier bash version. bash v.4 was released in 2009.) (obsolete): Locate and open your limewire.props file found at ~/.limewire/limewire.props and type into a fresh line the following text: PATH_TO_BLACK_LISTED_IP_ADDRESSES=Home/.limewire/hostiles.txt Save the file as standard text, keeping the .props file extension. (/obsolete) * Edit 14 May 2013: I just discovered on Linux the hostiles file needs to start without a capital or else it will not work. I have adjusted the files for linux. Sorry to anybody who might have been inconvenienced and thought these files did not work. The Linux files include manual instructions for both Linux, Windows and MacOSX. Linux Filenames: . linux_LW_Security_install.7z (recommended) - uses a script to install it. (Edit: the Manual lists are no longer being hosted! Not enough demand for them.) . Linux Manual Light LW Security 2013, . Linux Manual Light LW Security-NJ 2013, . Linux Manual Strong LW Security 2013, . Linux Manual Strong LW Security-NJ 2013. LimeWire clones are unable to utilize the hostiles file. I did create a multi-clone blocklist installer but discovered most LW clones did not use the hostiles. I find LuckyWire highly problematic to connect and only seem to be able to connect via forcing hosts. It's my guess it probably only works with LuckyWire and certainly seems to. The reason being most of the clones were earlier breakaways from the LW code before LW introduced the portable code options within the main code. What is a Hostile Host? - my definition: Nobody is pretending these lists will block out all spam but certainly greatly reduce it, and even better it will reduce chances of you connecting directly to known spam/hostile hosts. There's different types of spammers and hostile hosts. Some you may not be aware of due to their approaches. For example, some will ping your client to reduce your program's abilities at downloading, uploading, searching and even connections without attempting to connect, browse, or download from you. At worst the constant ping attacks (DDoS) will make you lose internet connection. Some will browse you as soon as and every time you log into the network. Then some may browse you robotically every 10-15 minutes for hours on end without downloading from you. Then there's some whom will attempt to fill and constrain your upload slots. This is a well known approach of theirs for many years. They will normally either choose your largest files to download all at once or your largest collection of files. -> These are all what I would refer to as hostiles. Spammers are 'almost' another category. And this is what the Hostiles list is about. Such recently identified hostiles are listed on the security lists to block them out. By recent I mean over the past 18 months because I only took upon this project this year and whilst aware of hostiles from the previous couple of years, I do not know the full history of the block list I inherited from the BearShare blocklist which had not been updated since June or earlier 2011. Download links for the LimeWire Security Updaters: (choose appropriate version for your system and your choice of security from the folders. Feel free to Bookmark any of these links to periodically check for updates): * LimeWire Security Updater installers via MediaFire * * LimeWire Security Updater installers via Sabercat * (Note: you need to use an up-to-date browser to use MediaFire. Pre-2013 Safari versions struggle to load their pages.) One other piece of spam and hostile host advice is, if you have any firewall or security software that can block ports, set up a rule to block ports 27016 and 7001 for both UDP and TCP which is only used by spam companies. Windows 7 instructions bottom half of post #31 here. If anything confuses you or you have any other questions, please feel free to ask. Also, if you find any problems with the installers or the way the security packages work, please let me know as soon as possible.  As mentioned at beginning of the post, these have been tested on both Windows and MacOSX with LW 4 and 5. Edit: And Linux, but the hostiles filename & props reference must not use a capital letter on Linux systems. The MediaFire link has 2 options for Linux users, .tar.gz compressed file which is about 3.4 MB or a .7z compressed file which is about 1.3 MB in size. As mentioned at beginning of the post, these have been tested on both Windows and MacOSX with LW 4 and 5. Edit: And Linux, but the hostiles filename & props reference must not use a capital letter on Linux systems. The MediaFire link has 2 options for Linux users, .tar.gz compressed file which is about 3.4 MB or a .7z compressed file which is about 1.3 MB in size.Another note, these blocklists might conflict with using torrents. Edit 18 September 2013, removed a character from each of the Full & Light Japanese block lists which prevented a range from working. Not sure how the odd character (looked like the letter a with a mark above it) became inserted, but it has since been removed. Last edited by Lord of the Rings; March 14th, 2013 at 10:54 AM. Reason: Updated notes. Windows now only one installer. Clone update |
 |
| |
 LinkBacks (?)
LinkBacks (?)
LinkBack to this Thread: https://www.gnutellaforums.com/limewire-wireshare-tips-tricks/81811-how-force-ultrapeer-better-searches-whether-using-pro-basic.html | ||||
| Posted By | For | Type | Date | |
| FTC responds to LabMD’s motion for sanctions in FTC v. LabMD » PHIprivacy.net | This thread | Refback | August 31st, 2014 01:25 PM | |
| Site Gnutella Forums | www.gnutellaforums.com | BoardReader | This thread | Refback | July 1st, 2011 01:02 PM | |
| Ultrapeer | Life123 | This thread | Refback | March 19th, 2011 02:27 PM | |
| Thread How to Force UltraPeer (Better searches whether using Pro or Basic) | Gnutella Forums | BoardReader | This thread | Refback | February 18th, 2011 10:40 PM | |